Security Audit Checklist
Cyber threats evolve daily, but your security posture doesn’t have to lag behind. This Security Audit Checklist transforms complex security frameworks into actionable defense strategies tailored to your threat landscape. From basic hygiene to advanced threat hunting, get a customized roadmap that security professionals actually use. Stop hoping you’re secure – know you are with systematic verification.
Physical Security
□ Perimeter security adequate
□ Access control systems functional
□ Badge system properly managed
□ Visitor management procedures followed
□ Security cameras operational and recording
□ Lighting sufficient in all areas
□ Alarm systems tested regularly
□ Guard services effective
□ Key management controlled
□ Secure areas properly restricted
□ Loading dock procedures enforced
□ Emergency exits accessible but secure
Information Security Policy
□ Security policy comprehensive and current
□ Standards documented and communicated
□ Procedures detailed and followed
□ Guidelines available and understood
□ Roles and responsibilities defined
□ Enforcement mechanisms in place
□ Exception process documented
□ Review cycle established
□ Training requirements specified
□ Compliance monitoring active
□ Violation consequences clear
□ Management support evident
Access Control
□ User provisioning process controlled
□ Identity verification performed
□ Authorization properly granted
□ Privileged access managed strictly
□ Password policies enforced
□ Multi-factor authentication deployed
□ Account reviews conducted regularly
□ Terminated access removed promptly
□ Service accounts inventoried
□ Generic accounts eliminated
□ Guest access controlled
□ Remote access secured
Network Security
□ Firewall configurations reviewed
□ Rules documented and justified
□ Segmentation implemented properly
□ DMZ configured correctly
□ Intrusion detection active
□ Intrusion prevention enabled
□ VPN access controlled
□ Wireless networks secured
□ Network monitoring continuous
□ Vulnerability scanning regular
□ Penetration testing performed
□ Patch management current
Data Protection
□ Data classification implemented
□ Sensitive data identified
□ Encryption requirements defined
□ Encryption properly implemented
□ Key management procedures secure
□ Data loss prevention active
□ Backup procedures verified
□ Recovery testing performed
□ Retention policies followed
□ Disposal procedures secure
□ Transit protection enforced
□ Storage security adequate
Application Security
□ Secure development practices followed
□ Security requirements defined
□ Design reviews conducted
□ Code reviews performed
□ Security testing completed
□ Vulnerability assessments done
□ Web application firewalls deployed
□ Input validation implemented
□ Authentication mechanisms secure
□ Session management proper
□ Error handling appropriate
□ Logging comprehensive
Endpoint Security
□ Antivirus software deployed
□ Signatures updated automatically
□ Personal firewalls enabled
□ Operating systems patched
□ Applications updated regularly
□ Unauthorized software prevented
□ Removable media controlled
□ Encryption enforced
□ Screen locks configured
□ Remote wipe capable
□ Asset inventory current
□ Configuration standards enforced
Security Operations
□ SOC operational 24/7
□ Monitoring tools configured properly
□ Alerts tuned effectively
□ Incident response procedures ready
□ Forensic capabilities available
□ Log collection comprehensive
□ Log retention adequate
□ Correlation rules effective
□ Threat intelligence integrated
□ Metrics tracked and reported
□ Improvements implemented
□ Team training current
Third-Party Security
□ Vendor risk assessments performed
□ Security requirements contractual
□ Compliance verification done
□ Access controlled strictly
□ Monitoring active
□ Incident notification required
□ Data protection enforced
□ Audit rights preserved
□ Insurance requirements met
□ Background checks completed
□ NDAs executed
□ Termination procedures defined
Incident Management
□ Incident response plan documented
□ Team members identified
□ Contact information current
□ Classification scheme defined
□ Escalation procedures clear
□ Communication plan ready
□ Technical procedures detailed
□ Evidence preservation understood
□ Recovery procedures tested
□ Lessons learned process active
□ Training conducted regularly
□ Exercises performed periodically
Compliance
□ Regulatory requirements identified
□ Standards adopted formally
□ Framework implemented
□ Controls mapped properly
□ Testing performed regularly
□ Evidence collected systematically
□ Gaps identified and addressed
□ Remediation tracked
□ Audits scheduled
□ Findings resolved timely
□ Certifications maintained
□ Improvements continuous
Security Awareness
□ Training program established
□ All employees trained
□ Annual refresher required
□ Role-based training provided
□ Phishing simulations conducted
□ Security tips communicated
□ Incident reporting encouraged
□ Policy acknowledgment required
□ Metrics tracked
□ Effectiveness measured
□ Program updated regularly
□ Management support visible
How the Security Audit Checklist works
Begin with your industry, data sensitivity level, and current security maturity. Describe your infrastructure and compliance requirements. The AI creates a prioritized security audit checklist covering technical controls, policies, and procedures. Each item includes implementation guidance, testing methods, and remediation timelines. Filter by criticality, compliance framework, or department. Generate executive summaries and technical appendices.
Data breaches cost millions, but most start with basic oversights. Generic security checklists miss your specific vulnerabilities. This tool builds defense-in-depth strategies that match your actual risks, not theoretical ones. It’s how security professionals systematically eliminate vulnerabilities before attackers find them. Don’t be tomorrow’s breach headline.
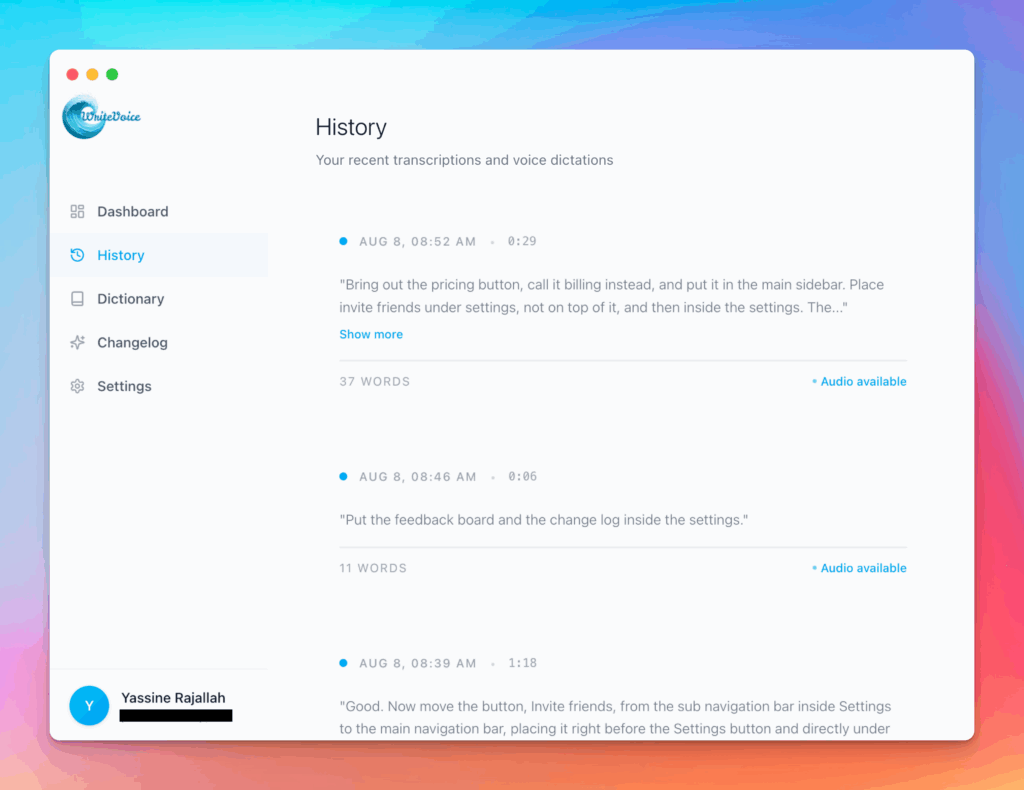
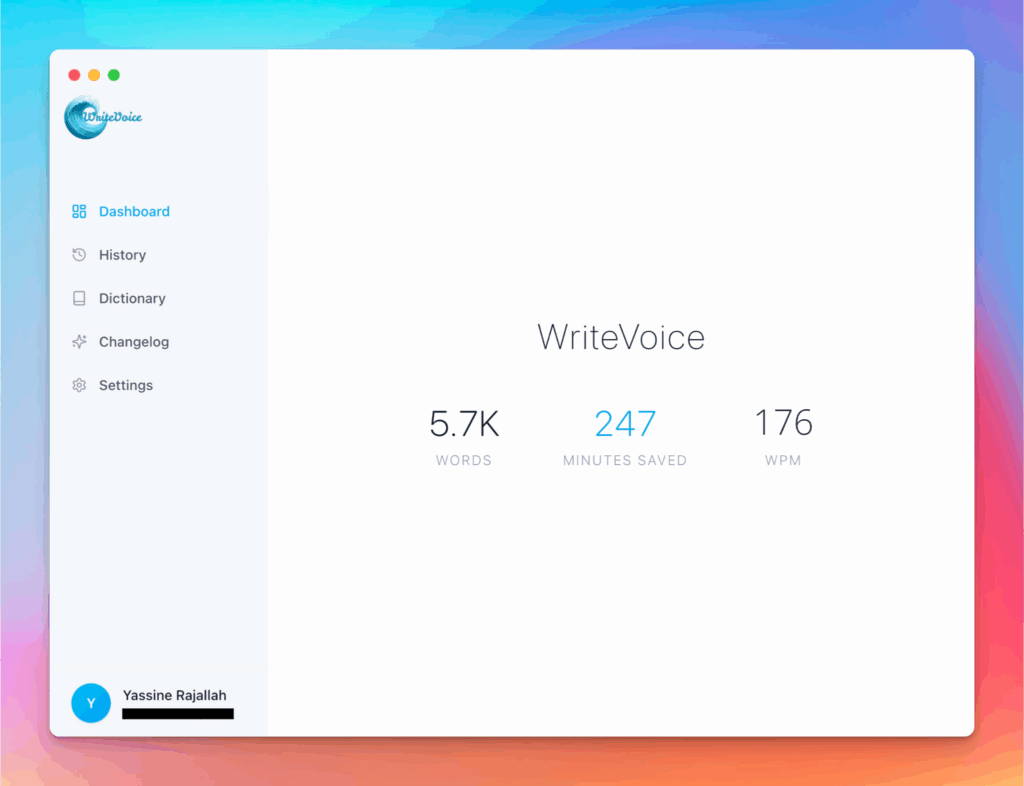
Meet the smartest dictation for auto-formatted and ready-to-send text
WriteVoice turns your voice into clean, punctuated text that works in any app. Create and ship faster without typing. Your first step was Security Audit Checklist; your next step is instant dictation with WriteVoice.
A blazing-fast voice dictation
Press a hotkey and talk. WriteVoice inserts accurate, formatted text into any app, no context switching
Works in any app
Press one hotkey and speak; your words appear as clean, punctuated text in Slack, Gmail, Docs, Jira, Notion, and VS Code—no context switching, just speed with writevoice
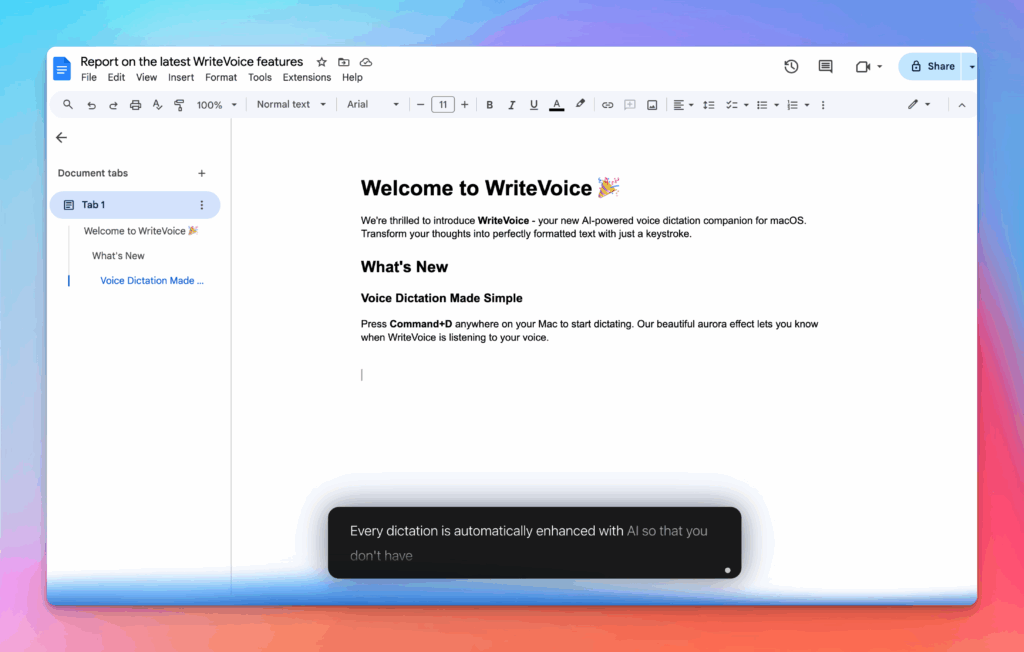
Accurate, multilingual, and smart
97%+ recognition, smart punctuation, and 99+ languages so your ideas land first try, built for teams and pros.
Private by default
Zero retention, audio and text are discarded instantly, with on-device controls so you can dictate sensitive work confidently.

